|
 FWPD West Division Newsletter
July 2024 Volume 2
|
|
First Responders Recognized at LVT Rise Community Center
The LVT Rise Community Center received a request from families that were impacted by the May 1st shooting in the Las Vegas Trail corridor. The families wanted to thank all of the first responders that were on scene to render aid and restore order during a very chaotic and tense situation. Councilmember Crain along with members of the FWPD and FWFD command staff including fellow fire fighters and police officers were in attendance.



|
|
Laundry Works hosts inaugural "Cones with a Cop" event
On Saturday, June 22, 2024, approximately 50 residents of the Las Vegas Trail area came out in the hot weather to enjoy eating some refreshing snow cones, play basket toss and enter their names in a drawing for a chance to win several $25.00 gift cards. Lincoln NPO Sergeant Owen as well as NPOs Grinalds (L16), Bryant (L18) and West Patrol officer Tennyson had the opportunity to meet wth the residents, try their hand at basket toss and cool off by enjoying a refreshing snow cone.



|
|
FWPD awards Moritz Kia a Certificate of Appreciation for hosting the ignition switch software upgrade event
FWPD West Division recognized Moritz Kia for its unwavering commitment to ensuring the safety of our communities. Specifically, the dealership was lauded for their dedication to assisting both vehicle owners and frontline police personnel in mitigating potential vehicle thefts. Lincoln District Lt. Hodges, Sgts. Stary and Reinhardt as well as NPOs Grinalds and Morquecho represented the department at the event.

|
|
Fraud & Scam Spotlight
Elder Fraud
Fox 4 News DFW recently ran the following story about how a good Samaritan called 911 and the quick actions by a North Texas police sergeant stopped a scammer from getting his hands on thousands of dollars.
Body camera footage provided by White Settlement police shows the actions taken to keep the victim from losing money. She told the sergeant someone from her bank's security team needed her to deposit her cash into a Bitcoin ATM.
Police say the scammer had been calling this elderly woman all week, threatening her and convincing her to send the money.
The scammer then set up an Uber to come pick the victim up from her retirement community and take her to a bank. She withdrew $40,000 and then was forced to go make the transaction.
White Settlement Police Sgt. James Stewart stepped in to stop an elderly woman in her 80s from sending tens of thousands of dollars to man claiming he was with Chase Bank.
"You still haven’t got her name right, you freaking moron," he told the scammer.
"Yeah, I was pretty curt and mean. I was irritated not just as a police officer but as a human being," Stewart told FOX 4.
However, the first person to take notice was Myndi Jordan. She stopped by the Chevron off I-30 and Cherry Lane Thursday for gas and cash. She says the woman still had wads of hundred-dollar bills in her purse. So she called 911.
"I noticed an elderly lady feeding thousands of dollars into the cryptocurrency machine. And the people on the phone sound like foreigners, and they are Facetiming to make sure she is putting the money in the machine," Jordan told 911.
"Can you go get her to stop?" the dispatcher asked.
"I tried. She said she’s trying to correct the mistake that somebody else made," Jordan said. "I just don’t… it’s so bad."
Jordan waited for Sgt. Stewart to arrive on scene. He told the woman to stop inserting money and took the phone.
The male voice on the other end continued to say he’s a Chase Bank security team member.
"Let me speak to the customer," the man on the phone said.
"No, you are not going to speak to the customer anymore. You have spoken to the customer enough," the sergeant told the man.
"She never hit the submit button," Stewart explained. "He kept saying, ‘Hit the ‘I’m done’ button.’ If she did that, the money would’ve been gone."
Jordan called the number on the Bitcoin machine to file a fraud report.
The woman will get her $23,000 back.
|
|
Internet Safety
Use Two-factor Authentication to Protect Your Accounts
Why a password alone isn’t enough
Like most people, you probably use a strong password to protect your accounts. But hackers use different tactics to steal or guess your passwords.
-
Hackers use phishing attacks to trick you into giving up your login credentials.
-
Scammers buy credentials stolen in data breaches, using your username and your password to log in to the account where the breach happened. (That’s why it’s important to change your password right away if you find out that your information may have been exposed in a breach.)
-
Hackers might also try to use the username and password to log in to another one of your accounts. This works only if you use the same username and password in more than one place — and is a reason to never reuse the same username and password.
-
If hackers only have your username, they can use software to guess your password. If the site doesn’t have safeguards to detect this type of attack, the hacker’s software may be able to try many different passwords.
Taking steps to keep your password secure is an important first line of defense against hackers. But the best way to protect your accounts is to use two-factor authentication, sometimes called two-step verification or multi-factor authentication.
Protecting your accounts
To prevent unauthorized access to your accounts, sites usually require you to sign in with a username and password. This process verifies who you are and is known as authentication. The credential you give to log in — your password, in this example — is a type of authentication factor. Authentication factors fall into three categories:
-
Something you know, like a password, a PIN, or the answer to a security question.
-
Something you have, like a one-time verification passcode you get by text, email, or from an authenticator app; or a security key.
-
Something you are, like your fingerprint, your face, or your retina.
Accounts with two-factor authentication require you to enter a credential from two of the three categories to log in.
Two factors are better than one
Using only one factor — say, something you know, like a password — to log in to your account is like having one lock on your front door. And not a very secure one.
Using two-factor authentication is like using two locks on your door — and is much more secure. Even if a hacker knows your username and password, they can’t log in to your account without the second credential or authentication factor.
The most common methods of authentication
More and more sites and apps are offering two-factor authentication. Some let you choose which authentication method to use. Others only give you one option. These are some of the most common authentication methods out there.
1. One-time passcode via text message or email
With this type of authentication, you get a verification passcode by text message or email. It’s typically six digits long but can be longer. It’s only good for one log in and expires automatically.
Getting a passcode by text message is a common and simple method of authentication that only requires a phone that can get text messages. But it has its drawbacks. Hackers can take over your phone number through a SIM card swap attack and get text messages sent to your number, including those with a verification code, before you realize someone stole your number.
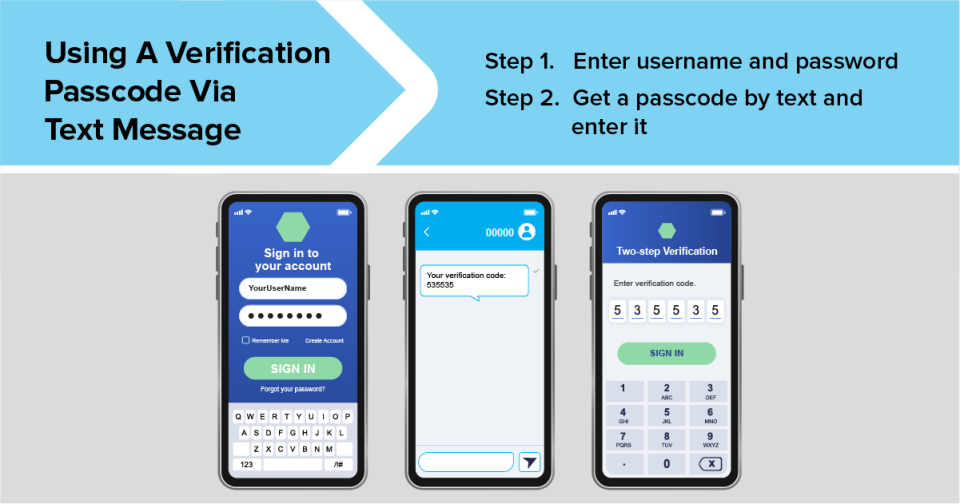
If you get a verification passcode by email, use a strong password and two-factor authentication on your email account. That’ll make it harder for someone to hack into your email and steal your one-time passcode.
Scammers try to trick you into giving them your verification passcode. No matter what the story is, don’t share your verification code with someone if you didn’t contact them first.
If getting a verification passcode by text message or email is the only option the account offers, it’s better than nothing. But it’s safer to use an authenticator app or security key, if they’re an option.
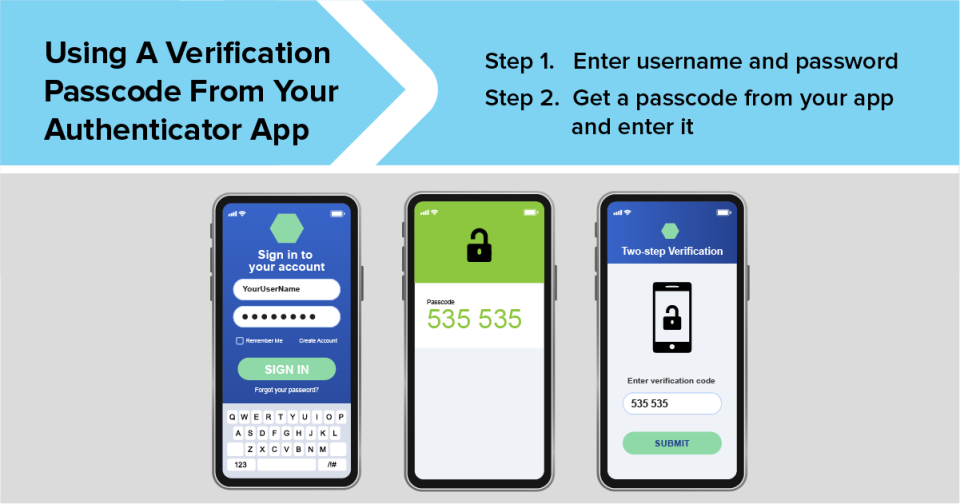
2. An authenticator app
Some accounts let you use an authenticator app on your phone or tablet to verify it’s you trying to log in. There are several authenticator apps out there, like Google Authenticator, Microsoft Authenticator, and Duo.
Authenticator apps typically generate a verification passcode, like one you might get by text message or email. But using an app is safer because the passcode isn’t susceptible to a SIM card swap attack or to someone hacking your email.
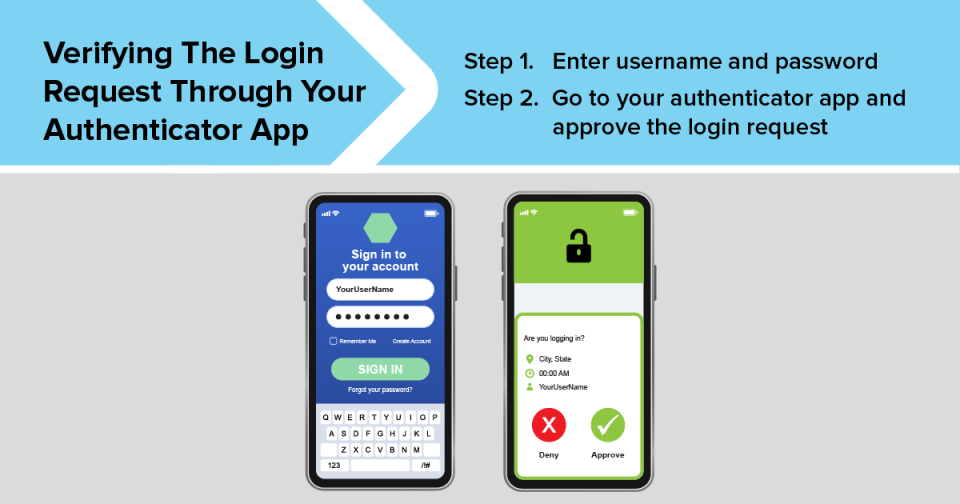
An authenticator app may also give you the option to get a push notification on your phone or tablet every time someone tries to log in to your account. The notification might give you some details about the login attempt, like the account someone is trying to log in to, their physical location, the type of device they’re using, and the date and time of the login attempt. You can approve or deny the request with a tap.
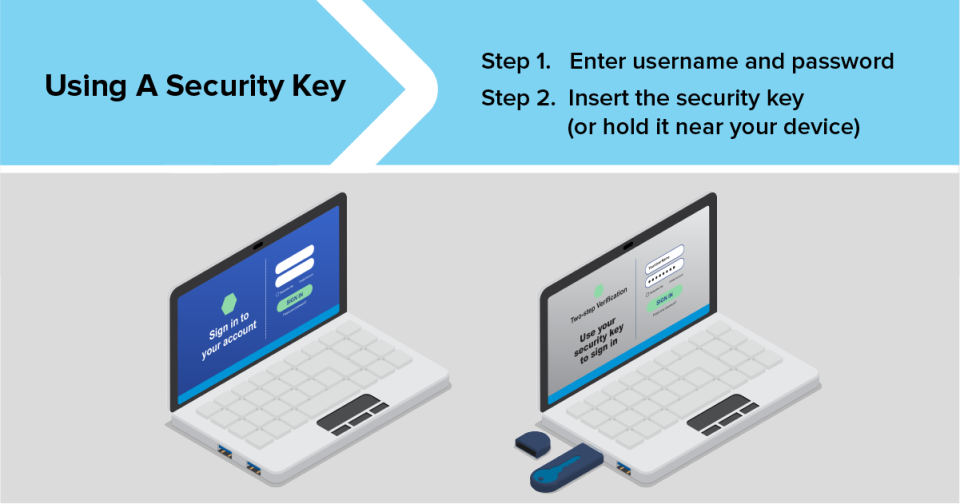
3. A security key
Security keys are physical devices that you use as your second authentication factor. They come in different shapes and sizes. You can buy one for personal use or you might get one from your employer.
Security keys use encryption to confirm that the key is associated with your account. Some plug into a USB port. Others use near-field communication (NFC) to connect to your device when you hold it close. Security keys are the strongest method of two-factor authentication because they don’t use credentials that hackers can steal.
Turning on two-factor authentication
More and more sites and apps are offering two-factor authentication, but it’s not usually on by default. To turn it on, go to your account settings, look for two-factor authentication, two-step verification, or multi-factor authentication, and follow the steps.
Start with your most sensitive accounts, like your bank, credit cards, email, social media, tax filing website, and payment apps. Then add it to other accounts, like sites you shop on.
After you set up two-factor authentication, you may have the option to remember the device you’re using to log in. If you do, instead of having to give the second credential every time you log in, you may only need to do so in certain situations, like when you log in from another device. Only have the account remember your own devices. Don’t have it remember the device if you’re logging in from a public computer, like at a library.
Two-factor authentication can add an extra layer of security that protects you from hackers. And spending a few minutes to turn it on now can save you the hassle — and countless hours — it’ll take to recover a hacked account or deal with identity theft.
|
|
NPO Corner
West Division NPOs make preparations for the Como July 4th Parade Celebration
Four West Division NPOs (Haddad, Janzen, Kuzenka and Pennington) are shown working diligently preparing 270 bags of candy that will be handed out during the Como July 4th parade.

|
|
NPO Roster

|
|
Overton Park_Tanglewood Communities hold annual July 4th Parade
NPO Janzen (K17) along with beat K17 day shift officer J. Thew participated in the annual Overton Park_Tanglewood Fourth of July Parade. Many vintage cars were on display along the parade route. As shown in the photos below, a great time was enjoyed by all who were in attendance.


|
|

Stephen Stous named West Division COP Coordinator
After serving for six years as the COP Coordinator for East Division, Stephen Stous has transferred to West Division replacing the retiring Gerald Huck. We look forward to working with Stephen as he continues to grow and sustain the COP program in West Division.
|
|
|
Immunization Collaboration of Tarrant County
Tarrant County Public Health is hosting several back-to-school immunization clinics. Exact locations, dates and times are listed in the flyer below.

|
|
Community Center Events
LVT Rise Community Center

Thomas Place Community Center

|
|
Crime Free Multi Housing
Attention: Apartment owners, managers, assistant managers and leasing agents. You can register to attend the city's Crime Free Multi Housing training by scanning the QR code to the right. |
|
 |
|
|
More context for a story or links to resources
|
|
|
|
|